Interview questions on tcp ip – Embark on an enlightening journey with our interview questions on TCP/IP, meticulously crafted to delve into the intricacies of this foundational protocol. Prepare to navigate through layers, handshakes, and addresses, gaining a comprehensive understanding that will empower you in any networking discussion.
TCP/IP, the cornerstone of modern communication, forms the backbone of the internet and countless applications. Dive deep into its structure, operation, and applications, equipping yourself with the knowledge to tackle any TCP/IP-related interview question with confidence.
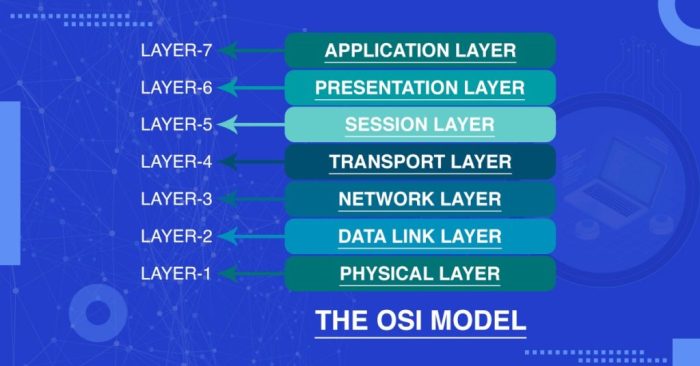
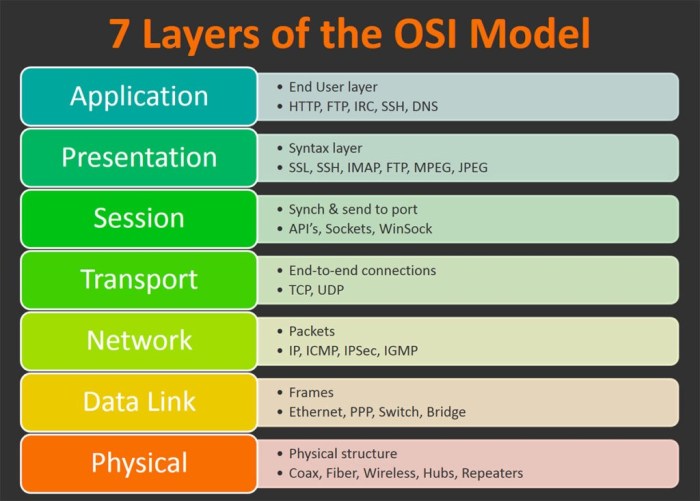
TCP/IP Overview

TCP/IP (Transmission Control Protocol/Internet Protocol) is a suite of communication protocols that allows computers to communicate over a network. It is the foundation of the Internet and other networks that use the Internet Protocol (IP). TCP/IP provides end-to-end data transmission services for applications running on different computers, ensuring that data is delivered reliably and in order.
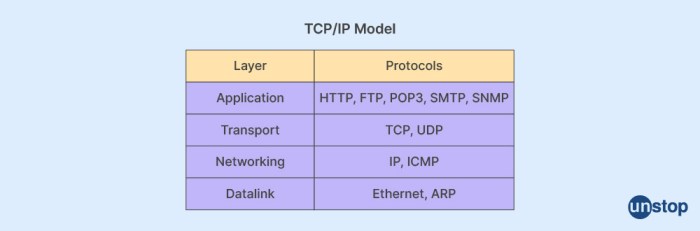
Layers of the TCP/IP Model
The TCP/IP model is a layered architecture that divides the communication process into four layers: the Application layer, the Transport layer, the Network layer, and the Link layer. Each layer has specific responsibilities and interacts with the layers above and below it to facilitate data transmission.
If you’re looking for some interesting interview questions on TCP/IP, you might also enjoy reading a memorable costume ASL story . It’s a great example of how to use creativity and humor to make a lasting impression. And who knows, you might even learn something new about TCP/IP in the process!
- Application layer:The Application layer provides a means for applications to access the network. It includes protocols such as HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), and SMTP (Simple Mail Transfer Protocol), which are used by applications to communicate with each other.
- Transport layer:The Transport layer provides reliable data transmission services to the Application layer. It includes protocols such as TCP (Transmission Control Protocol) and UDP (User Datagram Protocol), which ensure that data is delivered in the correct order and without errors.
- Network layer:The Network layer provides routing and addressing services to the Transport layer. It includes protocols such as IP (Internet Protocol) and ICMP (Internet Control Message Protocol), which are used to determine the path that data takes across the network and to handle error messages.
- Link layer:The Link layer provides physical connectivity to the network. It includes protocols such as Ethernet and Wi-Fi, which are used to transmit data over the physical medium, such as cables or wireless signals.
TCP Basics

TCP, or Transmission Control Protocol, is a vital component of the Internet protocol suite. It’s a reliable, connection-oriented protocol that ensures data is delivered from source to destination accurately and in the correct order.TCP operates by establishing a connection between two endpoints before any data transfer occurs.
This connection establishment process involves a three-way handshake, which we’ll discuss in detail shortly. Once the connection is established, TCP uses sequence and acknowledgment numbers to ensure reliable data delivery.
Three-Way Handshake
The TCP three-way handshake is a crucial step in establishing a reliable connection. It involves the following steps:1.
-
-*SYN (Synchronize)
The initiating endpoint sends a SYN packet to the receiving endpoint, requesting a connection.
- 2.
- 3.
-*SYN-ACK (Synchronize Acknowledgment)
The receiving endpoint responds with a SYN-ACK packet, acknowledging the SYN request and sending its own SYN packet.
-*ACK (Acknowledgment)
The initiating endpoint sends an ACK packet, acknowledging the SYN-ACK packet and completing the connection establishment.
This handshake ensures that both endpoints are ready to exchange data and have synchronized their sequence numbers.
Sequence and Acknowledgment Numbers
TCP uses sequence and acknowledgment numbers to track the flow of data and ensure its reliable delivery.*
-*Sequence numbers
Each packet sent by an endpoint has a sequence number. This number indicates the order in which the packet was sent.
-*Acknowledgment numbers
When an endpoint receives a packet, it sends an acknowledgment packet with an acknowledgment number. This number indicates the next sequence number it expects to receive.By using sequence and acknowledgment numbers, TCP can detect and recover from lost or out-of-order packets, ensuring that data is delivered accurately and in the correct order.
IP Addressing
IP addressing is a fundamental concept in TCP/IP networks, providing a unique identifier for each device connected to the network. An IP address is a 32-bit numerical label that identifies a host or network interface.
Structure of IP Addresses
An IP address consists of two parts: the network portion and the host portion. The network portion identifies the network to which the host belongs, while the host portion identifies the specific host within that network.
Types of IP Addresses
There are two main types of IP addresses: IPv4 and IPv6.
- IPv4: The most widely used IP address format, consisting of four octets (8-bit numbers) separated by periods (.). Each octet can range from 0 to 255, resulting in a total of 4.3 billion possible addresses.
- IPv6: The successor to IPv4, designed to address the shortage of IPv4 addresses. IPv6 addresses consist of eight 16-bit hexadecimal numbers separated by colons (:). The total number of possible IPv6 addresses is significantly larger than IPv4, at 3.4 x 10^38.
IP Address Classes
IPv4 addresses are classified into five classes (A, B, C, D, and E), each with a different range of network and host portions. The first octet of an IPv4 address determines the class.
| Class | First Octet Range | Network Portion | Host Portion |
|---|---|---|---|
| A | 1-126 | 8 bits | 24 bits |
| B | 128-191 | 16 bits | 16 bits |
| C | 192-223 | 24 bits | 8 bits |
| D | 224-239 | – | – |
| E | 240-255 | – | – |
Subnetting
Subnetting is a technique used to divide a network into smaller subnetworks, allowing for more efficient use of IP addresses. Subnetting involves dividing the host portion of an IP address into subnets, creating multiple smaller networks within the original network.
Valid and Invalid IP Addresses
A valid IP address must conform to the following rules:
- Each octet must be a number between 0 and 255.
- The first octet cannot be 0.
- The last octet cannot be 255.
Examples of valid IP addresses:
- 192.168.1.1
- 10.0.0.1
- 2001:0db8:85a3:08d3:1319:8a2e:0370:7334
Examples of invalid IP addresses:
- 0.0.0.0
- 255.255.255.255
- 192.168.0.256
- 2001:0db8:85a3:08d3:1319:8a2e:0370:ffff
Routing Protocols
Routing protocols are essential components of any network, as they enable devices to communicate with each other by exchanging information about the network topology and the best paths to reach different destinations. They play a crucial role in maintaining network connectivity, optimizing traffic flow, and ensuring efficient data delivery.
Operation of Routing Protocols
Routing protocols operate by exchanging routing information between routers, which are devices responsible for forwarding data packets between networks. Routers use this information to build and maintain routing tables, which contain the best known paths to different destinations. When a router receives a data packet, it checks its routing table to determine the next hop for the packet and forwards it accordingly.
Types of Routing Protocols
There are various routing protocols available, each with its own strengths and weaknesses. Some of the most commonly used protocols include:
- RIP (Routing Information Protocol):RIP is a simple and widely used distance-vector routing protocol that operates on small networks. It uses hop count as the metric for determining the best path.
- OSPF (Open Shortest Path First):OSPF is a link-state routing protocol that uses the Dijkstra algorithm to calculate the shortest path to each destination. It provides faster convergence and more efficient routing compared to RIP.
- BGP (Border Gateway Protocol):BGP is a path-vector routing protocol that is used for inter-domain routing between different autonomous systems. It allows for more flexible routing policies and supports complex network topologies.
TCP/IP Applications
TCP/IP plays a pivotal role in various applications that underpin modern communication and networking.
Let’s delve into some common TCP/IP applications and their impact on everyday activities:
Web Browsing
When you access a website, your web browser initiates a TCP connection to the web server hosting the site. TCP ensures reliable data transmission, ensuring that web pages, images, and other content are delivered to your device without errors or loss.
Email relies on TCP/IP for both sending and receiving messages. SMTP (Simple Mail Transfer Protocol) uses TCP to establish a connection between email clients and servers, ensuring the secure and reliable delivery of emails.
File Transfer
FTP (File Transfer Protocol) utilizes TCP to facilitate the transfer of files between computers over a network. TCP provides a reliable and efficient mechanism for transmitting files, ensuring that data is not lost or corrupted during the transfer process.
Impact on Modern Communication and Networking, Interview questions on tcp ip
TCP/IP has revolutionized modern communication and networking by enabling the seamless exchange of data and information across various platforms and devices.
- TCP/IP’s reliability and efficiency have made it the foundation of the internet, allowing for the widespread adoption of web-based applications and services.
- TCP/IP’s versatility has fostered the development of new technologies and protocols, such as VoIP (Voice over IP) and video conferencing, which rely on TCP/IP for reliable and real-time data transmission.
- TCP/IP’s scalability has allowed for the growth and expansion of the internet, enabling billions of devices to connect and communicate globally.
Top FAQs: Interview Questions On Tcp Ip
What is the purpose of TCP/IP?
TCP/IP (Transmission Control Protocol/Internet Protocol) is a suite of protocols that enables communication between devices on a network. It ensures data is transmitted reliably and efficiently, forming the foundation of the internet and various applications.
Explain the three-way handshake in TCP.
The three-way handshake is a process used to establish a TCP connection between two devices. It involves three steps: SYN (synchronize), SYN-ACK (synchronize-acknowledge), and ACK (acknowledge), ensuring a reliable connection before data transmission.
What is the difference between a static and a dynamic IP address?
A static IP address remains constant, while a dynamic IP address is assigned temporarily to a device when it connects to a network. Static IP addresses are useful for servers and other devices that require a permanent address, while dynamic IP addresses are commonly used for home and mobile devices.